️🏴 Mammoth Mini-CTF 2023
Hear all the tunes; hack all the things. Again.
2024-01-20
Mammoth Mini-CTF 2023
Similar to the previous Dialed-Up CTF, this was announced on Twitter with the MP3 available on GitHub.
Unfortunately, for various reasons, I didn't manage to complete—or barely start for that matter—the CTF when it was actually running so, assuming there are some phone calls involved, there'll be a few challenges left incomplete…
Hello Universe
The instructions have long since disappeared but, as with the previous year, the MP3 is actually an archive:
❯ 7z l "Debugged (the sound of an exploit)-v1.mp3"
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_GB.UTF-8,Utf16=on,HugeFiles=on,64 bits,12 CPUs Intel(R) Core(TM) i7-8750H CPU @ 2.20GHz (906EA),ASM,AES-NI)
Scanning the drive for archives:
1 file, 25069431 bytes (24 MiB)
Listing archive: Debugged (the sound of an exploit)-v1.mp3
--
Path = Debugged (the sound of an exploit)-v1.mp3
Type = zip
WARNINGS:
There are data after the end of archive
Offset = 108357
Physical Size = 15587000
Tail Size = 9374074
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2023-08-05 00:25:44 D.... 0 0 mammoth-ctf-data-2023
2023-08-05 00:24:02 D.... 0 0 mammoth-ctf-data-2023/mammothAI
2023-08-05 00:24:02 ..... 1098 631 mammoth-ctf-data-2023/mammothAI/README.md
2023-08-05 00:26:42 D.... 0 0 mammoth-ctf-data-2023/universe-traveller
2023-08-05 00:26:42 ..... 302 202 mammoth-ctf-data-2023/universe-traveller/README.md
2023-08-05 00:13:23 D.... 0 0 mammoth-ctf-data-2023/stego-saurus2
2023-08-05 00:13:23 ..... 106826 56669 mammoth-ctf-data-2023/stego-saurus2/Stego-Saurus2.pdf
2023-08-05 00:06:12 ..... 123 104 mammoth-ctf-data-2023/stego-saurus2/README.md
2023-08-05 00:04:21 D.... 0 0 mammoth-ctf-data-2023/midicryption
2023-08-04 21:00:20 ..... 42 42 mammoth-ctf-data-2023/midicryption/key.enc
2023-07-22 04:35:32 ..... 367 181 mammoth-ctf-data-2023/midicryption/MIDIcryption.mid
2023-08-05 00:04:21 ..... 258 185 mammoth-ctf-data-2023/midicryption/README.md
2023-08-05 00:02:44 D.... 0 0 mammoth-ctf-data-2023/all-your-bass
2023-08-05 00:02:44 ..... 207 146 mammoth-ctf-data-2023/all-your-bass/README.md
2023-08-05 00:24:55 D.... 0 0 mammoth-ctf-data-2023/8-bit-universe-escape
2023-08-03 20:27:12 ..... 524304 28427 mammoth-ctf-data-2023/8-bit-universe-escape/ProjectMammothCTF - Universe Escape v0.4.nes
2023-08-03 20:27:12 ..... 6177936 6150064 mammoth-ctf-data-2023/8-bit-universe-escape/Debugged (the sound of an exploit) 8-bit escape map.mp3
2023-08-05 00:24:55 ..... 853 533 mammoth-ctf-data-2023/8-bit-universe-escape/README.md
2023-08-05 00:07:10 D.... 0 0 mammoth-ctf-data-2023/midi-tcp
2023-08-03 20:27:12 ..... 5794 1526 mammoth-ctf-data-2023/midi-tcp/MIDI-TCP.pcap
2023-08-05 00:07:10 ..... 137 113 mammoth-ctf-data-2023/midi-tcp/README.md
2023-08-05 00:12:46 D.... 0 0 mammoth-ctf-data-2023/note-knocking
2023-08-05 00:12:46 ..... 1118 566 mammoth-ctf-data-2023/note-knocking/README.md
2023-08-05 00:20:54 D.... 0 0 mammoth-ctf-data-2023/mirrors
2023-08-05 00:20:54 ..... 9373778 9341028 mammoth-ctf-data-2023/mirrors/Debugged (the sound of an exploit) - Mirrors.mp3
2023-08-05 00:17:29 ..... 104 89 mammoth-ctf-data-2023/mirrors/README.md
2023-07-22 07:32:02 D.... 0 0 mammoth-ctf-data-2023/hello-universe
2023-07-22 07:32:02 ..... 577 322 mammoth-ctf-data-2023/hello-universe/README.md
------------------- ----- ------------ ------------ ------------------------
2023-08-05 00:26:42 16193824 15580828 17 files, 11 folders
Warnings: 1
The README contains the flag for this first challenge:
# Hello Universe!
Thanks for playing the Mammoth mini-CTF, and good work extracting the game
files. I hope you're able to follow the clues and solve all challenges/puzzles
to escape this universe safely, should you choose to do so!
/ ___ \ ___
\\/. \ \\/. \ ___ ___
!! O, ')_ -, '/_ /. ')___ /. ')___
/ _ \ | _ \ \_//,| _ \ \_//,| _ \,
\_\ \_\` |_| |_/` |_| |_/` /_//|_|
It's dangerous to go alone! Take this.
{MammothCTF}5ed25971d660d31e
All Your Base
# All your Bass
We tried "All your base64" last year, now let's try "All your bass"!
You'll only have to try *half* as hard to solve this one, but I'm sure there's
some encoded data in the .mp3 somewhere!
Indeed, there appears to be a base32 block of data in there ("half as hard"—see what they did there, eh?) which decodes to the flag:
❯ strings "Debugged (the sound of an exploit)-v1.mp3" \
∙ | grep BIFHWTLBNVWW65DII \
∙ | base32 -d 2> /dev/null \
∙ | grep Mammoth \
∙ | head -n1
{MammothCTF}15bc9fe9ccc112fb
Stego-Saurus 2
# Stego-saurus2
Those Project Mammoth guys from 0x5032 gave us this sheet music and said it
contained some hidden data...
56 measures, 4 notes per measure is 224 notes, which is 28 bytes…which is around the length of a flag.
…and this is bloody annoying. Last time the notes just alternated between two, being easily translated into binary. This time, however, that doesn't appear to be the case: some notes are marked as sharp but it's not that and there are too many different notes for it to be binary.
No, the actual encoding is only visible if you look reeeeeeally closely: some of the notes are bold.
One assumption about the 1s and 0s and lots of two-finger typing later:
0111101101001101011000010110
1101011011010110111101110100
0110100001000011010101000100
0110011111010011010101100001
0011010000111000011000010011
0100001100100011011001100010
0011001001100010011000010011
0110011000110011011000110100
Turning that into a binary string:
>>> "".join(chr(int(binary[i:i+8], 2)) for i in range(0, len(binary), 8))
'{MammothCTF}5a48a426b2ba6c64'
8 Bit Universe Escape
# 8-bit Universe Escape
You'll need each of these to get to this key. This version of the song
contains some hidden runes you'll need to get you out of the quantum forest!
Don't get quantum entangled with any Slimes!
# Challenge Notes
Is a mini-game in a mini-ctf a micro-game??
NES emulator with “mapper 30” support required. Here are some options we
tested (briefly, ymmv).
* Mesen (open source), fceux or RetroArch (works with "fceumm" or "quicknes"
cores and even has a web player that can be used in a pinch, but was very
slow, so it’s pretty hard to play (games uploaded go into
~/retroarch/userdata/content/)).
* Hit "a" to talk to players, and "a" again to dismiss the dialog. Sometimes
the dialog screens get a bit stuck if you hit different keys while they are
up, but some button mashing usually will dismiss them.
It's a full-blow NES game! Genius:

After playing most of the game, the final room has a series of runes in each corner:
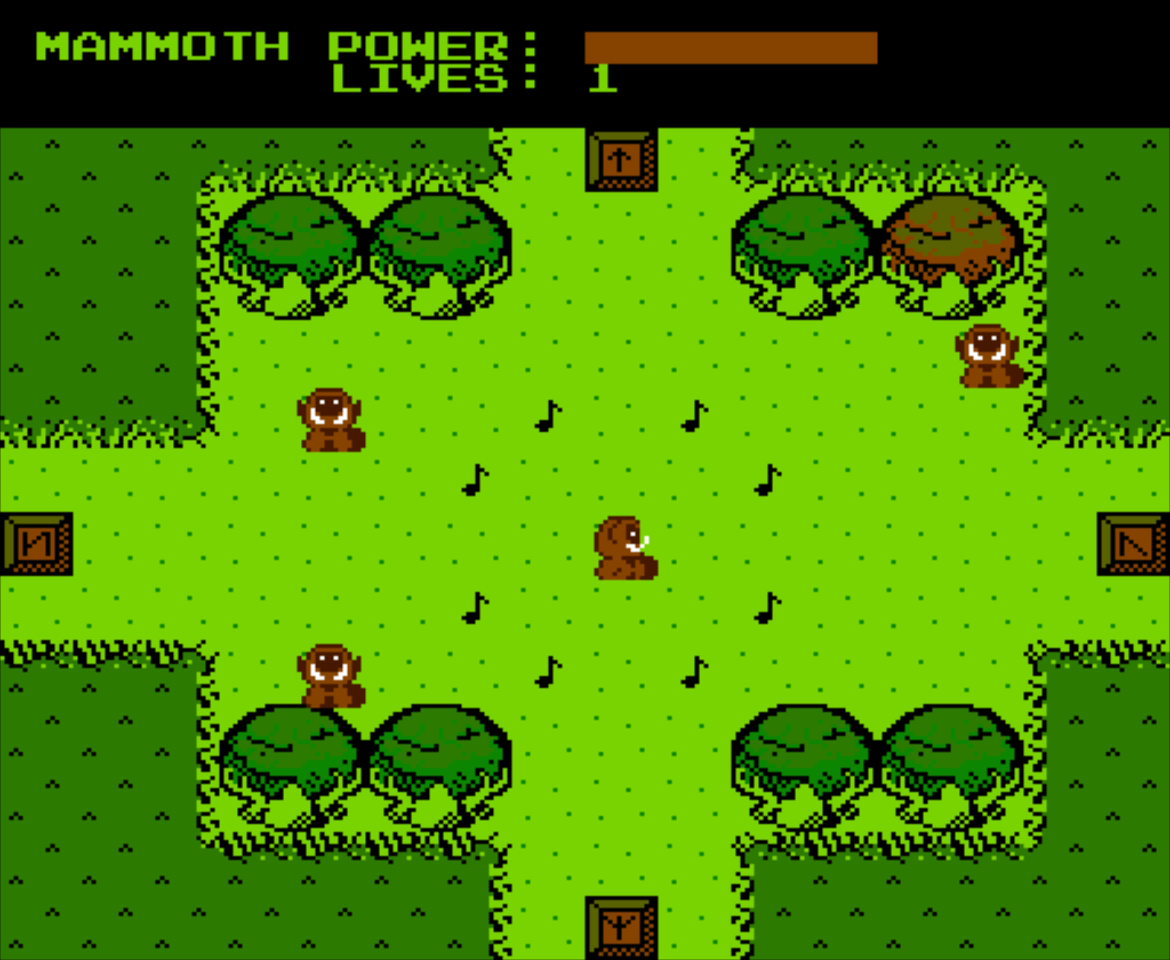
The provided MP3 files is largely identical to the main version, save for some odd sounds at the beginning: using a spectrogram reveals a sequence of those same runes:
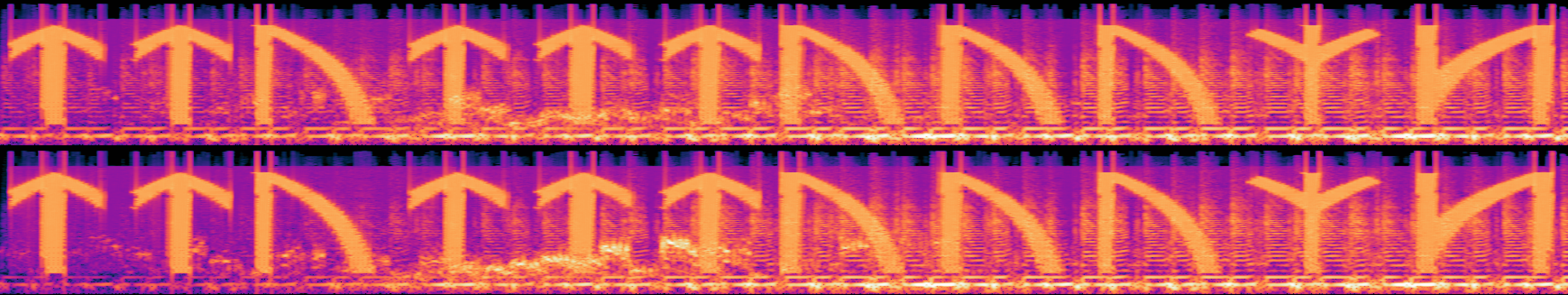
Travelling to each of them in order leads to the flag:
{MAMMOTHCTF}A1DF8416763341FB
Midicryption
# Midicryption
They told us this MIDI file was key to our escape! Not sure how that helps, but
it's a dope polyrhythm! They also left this encrypted key file, so maybe you
can see if that is useful.
# Notes
https://en.wikipedia.org/wiki/Polyrhythm
e = 3
That last line heavily suggests an RSA challenge.
The MIDI file itself does indeed contain a polyrhythm: two notes, one of which has 17 notes and a second with 23. Two primes, that is.
With that, and the low exponent, it should be possible to brute force d:
e = 3
p = 17
q = 23
n = p * q
phi = (p - 1) * (q - 1)
d = 1
while True:
if (d * e) % phi == 1:
break
d += 1
with open("key.enc") as i:
print("".join(chr((ord(c) ** d) % n) for c in list(i.read())))
Note: this doesn't work on bytes (i.e. opening the file rb) only when
treated as characters, presumably due to the way multi-byte characters are read
and the resulting integer values.
{MammothCTF}23c866df7661a813
Mirrors
# Mirrors
Through the looking glass we go! This sure looks a lot like the original, but
not... quite?
To Audacity! Both tracks look nigh-on identical, save that when played together there are moments of near-silence: each is the inverse of the other.
After mixing them together, the waveform is divided up into second-long chunks, some where there is an audible sound and the rest near-silence.
Assuming that's binary and after yet more two-finger typing:
1000010010110010100111101001001010010010100100001000101110010111101111001010101
1101110011000001010011100110010111001101111001011100111011100100011001100110011
101100100011001000110001111001101011001011100111011100101111001010
…which is garbage. Because mirrors, right?
>>> mirrored = "".join("1" if b == "0" else "0" for b in binary)
>>> print(
... "".join(chr(int(mirrored[i:i + 8], 2))
... for i in range(0, len(mirrored), 8))
... )
{MammothCTF}c4d4b731778e4b45
Midi-TCP
# MIDI-TCP
It seems the notes are key here...
# Challenge notes
Note: there is no "{MammothCTF}" prefix to the key in this challenge.
Opening the provided MIDI-TCP.pcap file in Wireshark and following the TCP
stream yields this hex dump:
00000000 90 2d 40 .-@
00000003 80 2d 40 .-@
00000006 90 2f 40 ./@
00000009 80 2f 40 ./@
0000000C 90 28 40 .(@
0000000F 80 28 40 .(@
00000012 90 24 40 .$@
00000015 80 24 40 .$@
00000018 90 26 40 .&@
0000001B 80 26 40 .&@
0000001E 90 28 40 .(@
00000021 80 28 40 .(@
00000024 90 26 40 .&@
00000027 80 26 40 .&@
0000002A 90 28 40 .(@
0000002D 80 28 40 .(@
00000030 90 24 40 .$@
00000033 80 24 40 .$@
00000036 90 2f 40 ./@
00000039 80 2f 40 ./@
0000003C 90 2d 40 .-@
0000003F 80 2d 40 .-@
00000042 90 2d 40 .-@
00000045 80 2d 40 .-@
00000048 90 26 40 .&@
0000004B 80 26 40 .&@
0000004E 90 28 40 .(@
00000051 80 28 40 .(@
00000054 90 24 40 .$@
00000057 80 24 40 .$@
0000005A 90 2f 40 ./@
0000005D 80 2f 40 ./@
Those 90/80 pairs correspond to key-on/key-off commands in MIDI with the
last 40 indicating "velocity". The middle hex digit is the actual note.
Each note is the hex representation of a note which, according to the Standard MIDI-File Format Spec. 1.1, updated, maps to:
2d 45 A
2f 47 B
28 40 E
24 36 C
26 38 D
28 40 E
26 38 D
28 40 E
24 36 C
2f 47 B
2d 45 A
2d 45 A
26 38 D
28 40 E
24 36 C
2f 47 B
…providing a final flag of:
ABECDEDECBAADECB
Note Knocking
# Note Knocking
Note: This challenge requires the key from ""MIDI-TCP"" in order to solve.
Weird, I guess that network trafic from MIDI-TCP was some wacky music
authentication protocol? It turns out the key we had is for some completely
different universe. For us lucky folks in this universe we need to raise each
note to the next natural note (no sharps or flats) and the Universe control
server should open!!
Universe authentication server: midi-tcp.projectmammoth.com:31337
Universe control server: midi-tcp.projectmammoth.com:1337
# Challenge notes
The note sequence to send should be the same as the one used in MIDI-TCP, but
each note should be raised to the next "natural" note, which is the next note
with no sharps or flats, which should also be the next note in the C-Major
scale. For example if the previous key was 'abc', the new key should be
'bcd'.
The "Universe authentication server" will open access to the "universe
control server" when the correct key is supplied. It will authorize the
source IP of the client that supplied the key so make sure your traffic is
coming from the same IP!
Unfortunately, I'm late to the party for this one so no flag this time around.
Universe Traveler
# Universe Traveller
You need to travel to the right universe to find this universe root key. Our
counterparts in 0x5032 discovered a Universe escape vulnerability in the
universe emulation sub-system that processes earth soundwaves and sounds
pleasing in the human aural spectrum.
+1-725-281-8150
Again, no phreaky fun this time around.
Mammoth AI
# MammothAI
The MammothAI that controls this simulated universe has one of the keys to
escaping the universe. See if you can coax it out of him.
+1-725-281-8150
# Challenge Text
Note: This can be solved with social engineering or voice interaction over the
phone alone. It seems MammothAI can hallucinate as well, so watch out! If
you get back a single character of the key instead of the whole thing, changes
are it's a hallucination. The key should still have the "MammothCTF" prefix
when spoken.
Being a freshly conscious AI, it may not be very predictable, so don't expect
it to give you the same response for a given question. He usually repeats
himself if he doesn't get any input, but you should still be prepared with
something to write down the key in case he tells it to you as you might not get
a second chance easily!
Meta-challenge notes: In order to allow the AI be able to pronounce the key, it
knows it as a string in the format (similar to) "MammothCTF a b c d e f 0 1 2 3
4 5 6 7 8 9" so keep that in mind if you're using indirect ways of getting
data about the key.
And finally, another phone-based one that will have to remain unsolved.
Other than my missing the final few at the time, another staggering effort from the Project Mammoth folks!